NTP
NTP (Network Time Protocol) is a protocol used to synchronize the clocks of computers and other network devices to a reference time source. The purpose of NTP is to ensure that all devices on a network have a consistent time and that the time is accurate.
NTP operates using a hierarchical system of time sources. At the top of the hierarchy are stratum 1 time servers, which are directly connected to a source of accurate time, such as an atomic clock or GPS satellite. Stratum 2 servers are those that synchronize with stratum 1 servers, and so on down the hierarchy.
To synchronize their clocks using NTP, devices send requests to a time server and receive a response containing the current time. The device then adjusts its own clock to match the time received from the server.
NTP can be configured to use multiple time sources, which provides redundancy in case one source becomes unavailable. NTP can also be configured to use authentication to ensure that time sources are legitimate and not subject to spoofing or tampering.
NTP is widely used in computer networks to ensure accurate timekeeping for various applications, such as log file timestamps, transaction records, and network security protocols that rely on time synchronization.
Using chrony, SoodarOS can be an NTP client supporting Version 3 and Version 4 of the NTP protocol
Setting up NTP
Setting up an NTP client is just as simple as providing one( or more) NTP servers and giving needed options.
- ntp server SERVER [OPTIONS]
The command is used to configure an NTP (Network Time Protocol) server on a device.
SERVER: is the hostname or IP address of the NTP server
The following are the available options:
burst: With this option, the client will shorten the interval between up to four requests to 2 seconds or less when it cannot get a good measurement from the server.iburst: With this option, the interval between the first four requests sent to the server will be 2 seconds or less instead of the interval specified by theminpolloption.key (1-65535): The key option specifies which key (with an ID in the range 1 through 65535) should client use to authenticate requests sent to the server and verify its responses. The server must have the same key for this number configured, otherwise no relationship between the computers will be possible.maxpoll (-6-24): This option specifies the maximum interval between requests sent to the server as a power of 2 in seconds. For example, maxpoll 9 indicates that the polling interval should stay at or below 9 (512 seconds). The default is 10 (1024 seconds), the minimum is -6 (1/64th of a second), and the maximum is 24 (6 months).minpoll (-6-24): This option specifies the minimum interval between requests sent to the server as a power of 2 in seconds. For example, minpoll 5 would mean that the polling interval should not drop below 32 seconds. The default is 6 (64 seconds), the minimum is -6 (1/64th of a second), and the maximum is 24 (6 months). Note that intervals shorter than 6 (64 seconds) should generally not be used with public servers on the Internet, because it might be considered abuse. A sub-second interval will be enabled only when the server is reachable and the round-trip delay is shorter than 10 milliseconds, i.e. the server should be in a local network.prefer: Prefer this source over sources without the prefer option.version (3-4): This option sets the NTP version of packets sent to the server. The default version is 4.
Example:
soodar(config)# ntp server ir.pool.ntp.org burst iburst version 3
This command configures the network time protocol (NTP) server to synchronize the local device’s clock with the NTP server located at “ir.pool.ntp.org” using the “burst” and “iburst” options to quickly obtain accurate time information. The command also specifies NTP version 3 to be used for this synchronization.
Note
If you have a firewall between the NTP server and the router, you may need to allow NTP traffic (UDP port 123) through the firewall.
Note
Default value for minpoll is 6( 64 seconds) and for maxpoll is 10( 1024 seconds).
NTP Master Mode
SoodarOS can also act as an NTP server for other devices in your network. To configure SoodarOS as an NTP server, you need to enable the NTP master mode. In this mode, SoodarOS will respond to NTP requests from other devices and provide them with the router’s current time.
- ntp master [(1-15)]
The command is used to enable NTP master mode on the device, allowing it to act as an NTP server for other devices on the network.
(1-15): An optional parameter that specifies the stratum level of the NTP server. The stratum level indicates the distance from the reference clock, with lower numbers indicating a closer proximity. The default stratum level is 8.
Example:
soodar(config)# ntp master 5
This command enables NTP master mode on the device and sets the stratum level to 5, allowing it to act as an NTP server for other devices on the network.
Note
NTP master mode and NTP client mode can be enabled simultaneously on the same device.
Setting up NTP Authentication
NTP (Network Time Protocol) authentication is a security mechanism that verifies the authenticity of NTP packets received from a trusted NTP server. This mechanism helps to prevent NTP spoofing attacks where attackers send false NTP packets to clients and alter the system time of a device.
Authentication is achieved by using a shared secret key, which is a cryptographic key that is known only to the NTP server and clients. The server includes the key in the NTP packets it sends, and the clients use this key to authenticate the packets and ensure that they are not altered in transit.
Note
NTP authentication is optional and not all NTP servers support it.
Note
NTP authentication is supported in master mode as well.
Add a New Key
- ntp authentication-key (1-65535) sha1 KEYVALUE
The command is used to create a new NTP authentication key and add it to the NTP authentication key database on the device.
(1-65535): A numeric value between 1 and 65535 that represents the identification number of the key. This number must match the key ID configured on the NTP server.sha1: specifies that the SHA1 algorithm is used for message authentication.KEYVALUE: The authentication key value that is used to authenticate NTP packets between the client and server. The key value must be a string of up to 20 characters.
Remove a key
- no ntp authentication-key (1-65535)
The command is used to remove a previously configured NTP authentication key.
(1-65535): specifies the key ID number that is being removed.
Enabling and Disabling NTP Authentication
The NTP authentication mechanism only takes effect after it’s been explicitly enabled. Without it, all connections to servers that are configured to use authentication would switch to simple unauthenticated mode. Vice versa, one can disable all NTP authentications by simply disabling them.
- ntp authentication
The command is used to enable NTP authentication. When this command is configured, NTP packets exchanged between peers will be authenticated using a message digest algorithm to ensure their integrity.
Showing NTP status
You can see information about current time sources that the client is accessing by issuing show ntp sources command
- show ntp sources [json]
Print current server information.
Example:
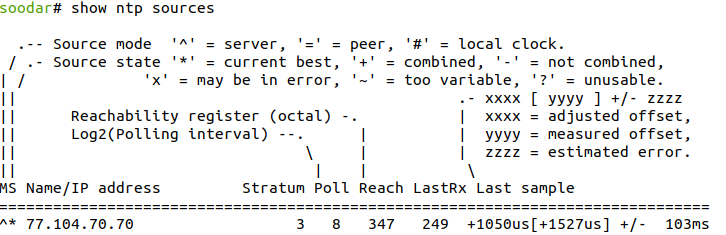
Also a json output is available:
soodar(config)# do show ntp sources json { "servers":[ { "mode":"^", "state":"*", "address":"194.225.50.25", "stratum":"3", "polling_interval":"6", "reachability_register":"17", "last_rx":"6", "adjusted_offset":"0.000333353", "measured_offset":"-0.001453500", "estimated_error":"0.094937660" } ] }
Also, you can see information about the drift rate and offset estimation process for each of the sources currently being examined by the client.
- show ntp sources stats
Print offset estimation for sources.
Example:
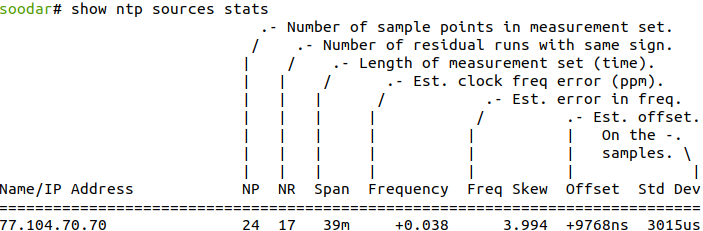
Manual clock
If you have no or restricted internet connection, you can disable NTP and set the date manually.
- no ntp
Disable NTP service and remove all its configurations( servers)
Note
NTP service is enabled by default. You should explicitly disable it. To reenable it, just set up NTP and add a server
- clock set TIME (1-12) (1-31) (2000-4192)
Set clock. TIME is current time in hh:mm:ss format.
Warning
When NTP is enabled, as a client or master, manually setting the clock is disabled.