Wireguard
WireGuard is a communication protocol and free and open-source software that implements encrypted virtual private networks, and was designed with ease of use, high-speed performance, and low attack surface.
SoodarOS supports Wireguard both as a wireguard server and as a wireguard client.
Interface
To start a wireguard tunnel, first, a wireguard interface should be created.
- interface wireguard (0-1023)
Create a wireguard interface instance.
- wireguard source A.B.C.D
Set wireguard tunnel source.
- wireguard private-key X25519KEY
Use x25519 key with
X25519KEYlabel as wireguard private key.
- wireguard port (1000-65535)
Wireguard’s UDP listens port. If not provided, use 51820 as the port.
Server
Each wireguard server instance can have multiple peers. Each peer consists of its public-key and allowed IPs( IP ranges that should be routed via tunnel).
- wireguard peer PEER
Create a wireguard peer named PEER
- public-key LINE [base64]
Peer’s x25519 public key in hexadecimal or base64
- allowed-ip A.B.C.D/M
Add A.B.C.D/M to peer’s allowed IP ranges.
Note
multiple ranges can be added by issuing allowed-ip command multiple times.
- no allowed-ip [A.B.C.D/M]
Remove A.B.C.D/M from peer’s allowed IP ranges. If run without any input, remove all allowed IPs.
- vrf VRF
Lookup peer destination in VRF’s FIB.
Client
A wireguard client instance has only one peer, and its peer is the server. This peer should have public-key, allowed IPs( IP ranges that should be routed via tunnel), the server address and its listening port.
- [no] endpoint A.B.C.D port (1000-65535)
Set/remove peer’s endpoint address and port.
Debug
Admin can see wireguard status by using show wireguard command.
- show wireguard [(1-1024) PEER] [json]
Show wireguard status. If the instance is not indicated, show all wireguards and their peers’ status. Users can specify which instance and which peer of that instance is in their interest. By adding
jsonoption to the command, output transforms to JSON.
server# show wireguard
Wireguard 10
Source: 200.1.3.1
Key: key1
Public key: 7D61BA2FA556FD7B4AA0D54114575DF6FBC5AB9B96337C4A438E85CDFC77ED7C
Port: 5100
Peer n3:
Public key: 950A6657CDE2193C786FF4771A46318AB86B9CB60BA071E344E8C094EBEEF662
Persistent keepalive: 25
Allowed IPs:
- 3.1.1.0/24
Wireguard 20
Source: 200.1.2.1
Key: key2
Public key: DF6DEA63D7F5E11F9115C1CAA08D78FAFE6BA003739952B8094BC7AE744D235A
Port: 5100
Peer n2:
Public key: 1D819A6950BBC16F04D86FBF8AA660434AEE12D77888E2F534641E9E7C51EEE2
Persistent keepalive: 25
Allowed IPs:
- 2.1.1.0/24
server# show wireguard 20
Wireguard 20
Source: 200.1.2.1
Key: key2
Public key: DF6DEA63D7F5E11F9115C1CAA08D78FAFE6BA003739952B8094BC7AE744D235A
Port: 5100
Peer n2:
Public key: 1D819A6950BBC16F04D86FBF8AA660434AEE12D77888E2F534641E9E7C51EEE2
Persistent keepalive: 25
Allowed IPs:
- 2.1.1.0/24
n3# show wireguard 10 server
Wireguard 10
Peer server:
Public key: 7D61BA2FA556FD7B4AA0D54114575DF6FBC5AB9B96337C4A438E85CDFC77ED7C
Endpoint: 200.1.3.1
Persistent keepalive: 25
Port: 5100
Allowed IPs:
- 1.1.1.0/24
server# show wireguard json
{
"wireguards":[
{
"instance":10,
"source":"200.1.3.1",
"key":"temp",
"public_key":"7D61BA2FA556FD7B4AA0D54114575DF6FBC5AB9B96337C4A438E85CDFC77ED7C",
"port":5100,
"peers":[
{
"name":"n3",
"public_key":"950A6657CDE2193C786FF4771A46318AB86B9CB60BA071E344E8C094EBEEF662",
"endpoint":"0.0.0.0",
"keepalive":25,
"port":0,
"allowed_ips":[
"3.1.1.0/24"
]
}
]
},
{
"instance":20,
"source":"200.1.2.1",
"key":"temp",
"public_key":"DF6DEA63D7F5E11F9115C1CAA08D78FAFE6BA003739952B8094BC7AE744D235A",
"port":5100,
"peers":[
{
"name":"n2",
"public_key":"1D819A6950BBC16F04D86FBF8AA660434AEE12D77888E2F534641E9E7C51EEE2",
"endpoint":"0.0.0.0",
"keepalive":25,
"port":0,
"allowed_ips":[
"2.1.1.0/24"
]
}
]
}
]
}
- show wireguard [(1-1024) PEER] stats [json]
n1# show wireguard stats
Wireguard 10
Peer n2:
Packets received: 0 packets, 0 bytes
Packets transmitted: 36 packets, 5328 bytes
Peer n1:
Packets received: 0 packets, 0 bytes
Packets transmitted: 0 packets, 0 bytes
Peer n3:
Packets received: 27 packets, 1676 bytes
Packets transmitted: 25 packets, 1568 bytes
n1# show wireguard 10 n3 stats
Wireguard 10
Peer n3:
Packets received: 36 packets, 2196 bytes
Packets transmitted: 31 packets, 1880 bytes
n1# show wireguard 10 n3 stats json
{
"wireguards":[
{
"instance":10,
"peers":[
{
"name":"n3",
"rx_packets":36,
"rx_bytes":2196,
"tx_packets":31,
"tx_bytes":1880
}
]
}
]
}
Example
In the following scenario, we want to establish a wireguard server with 3 clients.
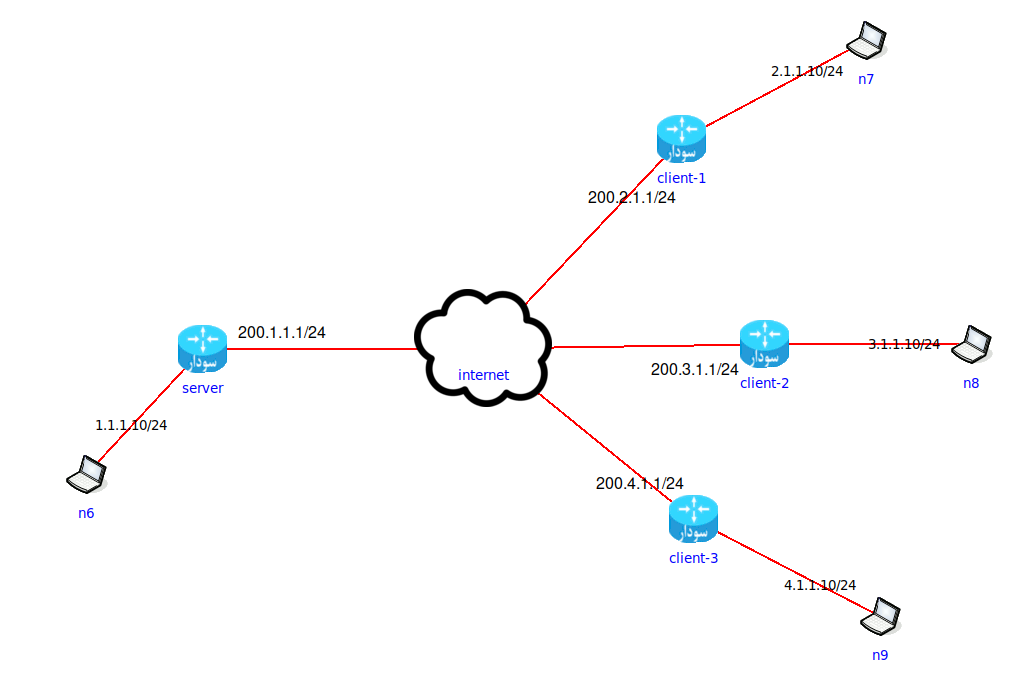
First, we create an x25519 private key in the server:
server(config)# crypto key generate x25519 label server-key
server# show crypto key server-key
Keypair Label: server-key
Algorithm: X25519
Public key: D889D845BEED407332B486A1C0A36D310781DD6BE2BB48855636125F16FC8142
Then we set up wireguard interface:
server(config)# interface wireguard 10
server(config-if)# wireguard source 200.1.1.1
server(config-if)# wireguard private-key server-key
server(config-if)# wireguard port 51820
Now we need to set up peers:
client-1(config)# crypto key generate x25519 label client1-key
client-1# show crypto key client1-key
Keypair Label: client1-key
Algorithm: X25519
Public key: 85DC0E1B1E8FA87B544863BD44FB7809B85853E4B1FF16E0EFAC70990BA17467
client-1(config)# interface wireguard 1
client-1(config-if)# wireguard private-key client1-key
client-1(config-if)# wireguard source 200.2.1.1
client-1(config-if)# wireguard port 51820
client-1(config-if)# wireguard peer server
client-1(config-wg-peer)# allowed-ip 1.1.1.0/24
client-1(config-wg-peer)# public-key D889D845BEED407332B486A1C0A36D310781DD6BE2BB48855636125F16FC8142
client-1(config-wg-peer)# endpoint 200.1.1.1 port 51820
We do the same thing for the remaining two clients.
Now that peers are set up, we add peer information to the server:
server(config)# interface wireguard 10
server(config-if)# wireguard peer client-1
server(config-wg-peer)# allowed-ip 0.0.0.0/0
server(config-wg-peer)# public-key 85DC0E1B1E8FA87B544863BD44FB7809B85853E4B1FF16E0EFAC70990BA17467
server(config-if)# wireguard peer client-2
server(config-wg-peer)# allowed-ip 0.0.0.0/0
server(config-wg-peer)# public-key 5A0882D0D6B757692FDCDFC7BB2413042A333F96EECEE34B69D0E2D7107C7672
server(config-if)# wireguard peer client-3
server(config-wg-peer)# allowed-ip 0.0.0.0/0
server(config-wg-peer)# public-key 87BC5D410DCDED2D5A9CC443053AC2888947E9724C247CE1FCBE40E12A400293
Now on the first packet from each client to 1.1.1.0/24, the tunnel establishes.